Sony utility disables UAC
March 25, 2013 Leave a comment
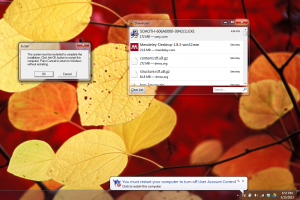
Sony Hotkeys Utilities (SOAOTH-606A0000-0042.exe) disables User Account Control (UAC) on my Windows 7 machine.
After re-installing Windows 7 on my Sony laptop I wanted to make my hotkeys (like volume) work again so I installed the Hotkeys utility by Sony. A few weeks later I got suspicious when several programs I opened had “Administrator:” in the title when I hadn’t approved any UAC. I checked my logs and the last program to ask for privilege elevation was the Hotkey utility.
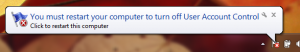
I re-enabled UAC dialogs and re-booted the machine. I re-downloaded the utility from Sony, installed it, and was asked to approve a UAC dialog (so UAC was definitely enabled). Sony software asked that I reboot the machine to “finish installation.” Immediately after the Sony dialog appeared a balloon in the bottom right appeared with the following text: “You must restart your computer to turn off User Account Control.” Sony’s software was the only thing running and I hadn’t opened any User Account Control settings since restarting the computer.
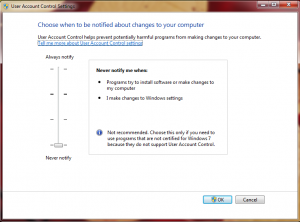
I let the software reboot the computer. After the reboot Sony software continued to install itself. I opened the User Account Control settings panel and verified that UAC was disabled.
Sony’s software finished installing itself, theoretically requiring UAC to do so, and asks to reboot a second time. I allowed it to reboot the machine and after the second reboot I pulled up the UAC settings again to verify that they were still disabled. As can be seen below the settings stayed with UAC disabled after two reboots.
Turning off UAC dialogs without user notification is a very dangerous thing to do. My computer spent several weeks in a state where any program that wanted to install could just do so without my approval. My programs were running with “Administrator” in the title because they were running with Administrator privileges (I manually verified this for PowerShell). No well behaved software should ever change security settings on a computer without notifying the user.
A couple of limitations to consider
- This is one personal computer, it is possible that the Sony utility is reacting badly with my computer’s setup.
- I tried the above steps three separate times, this is repeatable (at least on my machine).